
https://dreamhack.io/wargame/challenges/433
XSS Filtering Bypass
Description Exercise: XSS Filtering Bypass에서 실습하는 문제입니다. 문제 수정 내역 2023.08.04 Dockerfile 제공
dreamhack.io

문제 제목을 보아하니, xss 필터링을 우회해서 푸는 문제인 것 같다.
일단 문제 웹페이지를 분석하고, 그 다음에 받은 문제 파일도 분석해보도록 하겠다.
[1] 문제 분석
# 문제 페이지 분석

초기 화면이다.
(1) /vuln(xss) page

/vuln(xss) page 를 들어가보면 나오는 화면.

<img> 태그가 사용되었다.
src는 이미지 파일의 URL을 지정하고,
따라서 웹 페이지에서 해당 https://dreamhack.io/assets/img/logo.0a8aabe.svg에 있는 이미지를 표시하도록 한다.
(2) /memo

memo 페이지에 들어갈 때 마다 'hello'가 출력된다.
URL에 /memo?memo=hello 부분을 보면 GET 방식을 사용하고 있음을 알 수 있다.
/memo 페이지에 파라미터 memo에 hello를 입력하여 전송했다는 의미로 받아들일 수 있다.

그렇기 때문에 ?memo=hi를 전송하면 "hi"라는 메세지가 이 페이지에 출력되는 것을 확인할 수 있다.
이 페이지의 소스 코드는 아래와 같다,
<!doctype html>
<html>
<head>
<link rel="stylesheet" href="/static/css/bootstrap.min.css">
<link rel="stylesheet" href="/static/css/bootstrap-theme.min.css">
<link rel="stylesheet" href="/static/css/non-responsive.css">
<title>Index XSS-Filtering-Bypass</title>
<style type="text/css">
.important { color: #336699; }
</style>
</head>
<body>
<!-- Fixed navbar -->
<nav class="navbar navbar-default navbar-fixed-top">
<div class="container">
<div class="navbar-header">
<a class="navbar-brand" href="/">XSS-Filtering-Bypass</a>
</div>
<div id="navbar">
<ul class="nav navbar-nav">
<li><a href="/">Home</a></li>
</ul>
<ul class="nav navbar-nav navbar-right">
</ul>
</div><!--/.nav-collapse -->
</div>
</nav>
<div class="container">
<pre>hello
hi
</pre>
</div> <!-- /container -->
<!-- Bootstrap core JavaScript -->
<script src="/static/js/jquery.min.js"></script>
<script src="/static/js/bootstrap.min.js"></script>
</body>
</html>
음... 알아낼 수 있는 것은 없었다.
(3) /flag

/flag 페이지의 화면이다.
지금까지 드림핵에서 풀었던 xss 문제들은,
입력 칸에 무언가를 입력하고 제출하면 /memo 페이지에 문제의 답인 FLAG가 출력되었었다.
아마 이 문제 또한 비슷한 방식일 것이라고 예상된다.
(다운받은 문제 파일을 살펴보면 알 수 있을 것이다.)
다음은 /memo 페이지의 소스 코드이다.
<!doctype html>
<html>
<head>
<link rel="stylesheet" href="/static/css/bootstrap.min.css">
<link rel="stylesheet" href="/static/css/bootstrap-theme.min.css">
<link rel="stylesheet" href="/static/css/non-responsive.css">
<title>Index XSS-Filtering-Bypass</title>
<style type="text/css">
.important { color: #336699; }
</style>
</head>
<body>
<!-- Fixed navbar -->
<nav class="navbar navbar-default navbar-fixed-top">
<div class="container">
<div class="navbar-header">
<a class="navbar-brand" href="/">XSS-Filtering-Bypass</a>
</div>
<div id="navbar">
<ul class="nav navbar-nav">
<li><a href="/">Home</a></li>
</ul>
<ul class="nav navbar-nav navbar-right">
</ul>
</div><!--/.nav-collapse -->
</div>
</nav>
<div class="container">
<form method="POST">
http://127.0.0.1:8000/vuln?param=<input type="text" name="param"/><br/>
<input type="submit"/><br/>
</form>
</div> <!-- /container -->
<!-- Bootstrap core JavaScript -->
<script src="/static/js/jquery.min.js"></script>
<script src="/static/js/bootstrap.min.js"></script>
</body>
</html>
이 코드에서 폼은 POST 방식으로 데이터를 전송하며,
"http://127.0.0.1:8000/vuln?param="으로 시작하는 URL로 데이터를 보낸다는 것을 알 수 있다.
# 문제 파일 분석
(1) app.py
#!/usr/bin/python3
from flask import Flask, request, render_template
from selenium import webdriver
from selenium.webdriver.chrome.service import Service
import urllib
import os
app = Flask(__name__)
app.secret_key = os.urandom(32)
try:
FLAG = open("./flag.txt", "r").read()
except:
FLAG = "[**FLAG**]"
def read_url(url, cookie={"name": "name", "value": "value"}):
cookie.update({"domain": "127.0.0.1"})
try:
service = Service(executable_path="/chromedriver")
options = webdriver.ChromeOptions()
for _ in [
"headless",
"window-size=1920x1080",
"disable-gpu",
"no-sandbox",
"disable-dev-shm-usage",
]:
options.add_argument(_)
driver = webdriver.Chrome(service=service, options=options)
driver.implicitly_wait(3)
driver.set_page_load_timeout(3)
driver.get("http://127.0.0.1:8000/")
driver.add_cookie(cookie)
driver.get(url)
except Exception as e:
driver.quit()
# return str(e)
return False
driver.quit()
return True
def check_xss(param, cookie={"name": "name", "value": "value"}):
url = f"http://127.0.0.1:8000/vuln?param={urllib.parse.quote(param)}"
return read_url(url, cookie)
def xss_filter(text):
_filter = ["script", "on", "javascript:"]
for f in _filter:
if f in text.lower():
text = text.replace(f, "")
return text
@app.route("/")
def index():
return render_template("index.html")
@app.route("/vuln")
def vuln():
param = request.args.get("param", "")
param = xss_filter(param)
return param
@app.route("/flag", methods=["GET", "POST"])
def flag():
if request.method == "GET":
return render_template("flag.html")
elif request.method == "POST":
param = request.form.get("param")
if not check_xss(param, {"name": "flag", "value": FLAG.strip()}):
return '<script>alert("wrong??");history.go(-1);</script>'
return '<script>alert("good");history.go(-1);</script>'
memo_text = ""
@app.route("/memo")
def memo():
global memo_text
text = request.args.get("memo", "")
memo_text += text + "\n"
return render_template("memo.html", memo=memo_text)
app.run(host="0.0.0.0", port=8000)
flag값을 찾아내는 것이 목표이므로, 우선 이 파일에서 'flag'라는 문자열이 들어간 부분을 먼저 보았다.
그러다보니 /flag 페이지의 구동 방식을 나타내는 '@app.route("/flag", methods=["GET", "POST"])'라는 부분을 먼저 보게되었다.
@app.route("/flag", methods=["GET", "POST"])

이 코드는 "/flag" 경로(페이지)에 대한 GET 및 POST 요청을 처리한다.
1. 만약 클라이언트가 GET 요청을 보낼 경우, "flag.html" 템플릿을 렌더링하여 반환한다.
2. 만약 클라이언트가 POST 요청을 보낼 경우, 요청으로부터 "param"이라는 이름의 폼 데이터를 가져온다.

(여기서 "param"이라는 폼 데이터를 가져오는 걸 말하는 것 같다.)
3. 그리고 check_xss 함수를 호출해 XSS 공격을 확인한다. 만약 xss 공격이 감지되면, "wrong??"이라는 경고 메세지를 포함한 자바 스크립트 코드를 반환하고 이전 페이지로 이동하도록 한다. 만약 xss 공격이 감지되지 않으면 "good"이라는 경고 메시지를 포함한 자바 스크립트 코드를 반환하고 이전 페이지로 이동하도록 한다.
.
.
.
그렇다고 한다.
그럼 xss 공격을 확인하는 check_xss 함수 부분을 살펴보자.
def check_xss(param, cookie={"name": "name", "value": "value"})
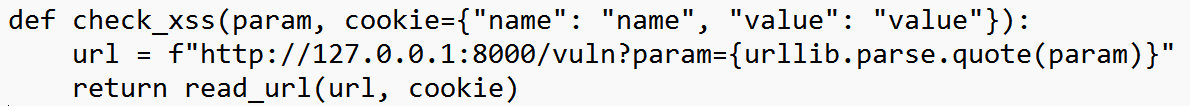
check_xss 함수는 param 값을 사용해 xss 공격 여부를 확인하기 위해
외부 URL (http://127.0.0.1:8000/vuln?param=<encoded_param>)로 요청을 보내고,
return_url 함수를 호출해 결과를 반환한다.
.
.
.
여기서 read_url 함수를 살펴보자.
def read_url(url, cookie={"name": "name", "value": "value"}):

이 함수의 내용에는 나도 모르는 내용이 많이 적혀있어서 찾아봤는데,
요약하면 read_url 함수는:
외부 URL에 대한 요청을 시뮬레이션하고, 해당 페이지에 쿠키를 전달한 후 XSS 공격 여부를 확인하는 데 활용된다고 한다.
.
.
.
여기서는 힌트를 얻지 못해서 app.py 파일 안의 다른 부분도 살펴보았다.
@app.route("/vuln")

이 부분은 "/vuln"(페이지)에 대한 부분이다.
코드 동작을 설명하자면,
1. GET 요청으로부터 "param" 쿼리 매개변수를 가져온다. 만약 "param"이 없으면 빈 문자열로 초기화한다.
2. 가져온 "param" 값을 xss_filter 함수로 전달하여 XSS 공격을 방지하도록 필터링한다.
3. 필터링된 "param" 값을 클라이언트에게 반환한다.
.
.
.
여기서 xss_filter 함수에서 어떻게 xss 공격을 방지하는지 알아보기 위해, xss filter 함수를 살펴보도록 하자.
def xss_filter(text):

이 함수에서는 주어진 텍스트에서 특정 XSS 공격과 관련된 문자열을 필터링하여 제거하는 역할을 한다.
좀 더 자세히 동작을 설명하겠다,:
1. _filter = ["script", "on", "javascript:"]:
필터링할 문자열 패턴을 담고 있는 리스트를 생성한다.
"script", "on", "javascript:"이 포함되어 있다.
2. for f in _filter::
_filter 리스트의 각 문자열을 순회한다.
3. if f in text.lower()::
주어진 텍스트에 대문자 또는 소문자로 변환한 문자열 중에 _filter의 원소가 포함되어 있는지 검사한다.
(대소문자를 무시하고 검사하기 위해 텍스트를 소문자로 변환한 후 검사하는 것.)
4. text = text.replace(f, ""):
텍스트에서 _filter에 해당하는 문자열을 제거한다.
만약 "script", "on", "javascript:" 가 포함되어 있다면 해당 문자열을 빈 문자열로 치환하여 제거한다.
5. return text:
필터링된 텍스트를 반환한다.
정리하자면
>> text를 모두 소문자로 변환하여 "script", "on", "javascript:"가 포함되어 있는지 검사하고, 있다면 해당 문자열을 빈 문자열로 치환하여 제거하는 것이다.
.
.
.
그렇다면 text 매개변수의 정확한 의미를 알기 위해 다른 부분도 살펴보았다.
@app.route("/memo")

이 부분을 훑어보니 def memo()에서의 'text'가 def xss_filter(text)에서 매개변수로 쓰이는 것 같았다.
좀 더 자세히 설명하자면,
memo 함수에서 text 변수에 할당된 값은 사용자가 "/memo"로 전송한 GET 요청의 "memo" 쿼리 매개변수에서 가져온 값이다.
이 text 변수는 이후 memo_text 변수에 추가되고, 그 결과가 템플릿으로 전달된다.
만약 이 text 값을 xss_filter 함수로 전달한다면, xss_filter 함수에서 정의된 필터링이 적용되어 XSS 공격을 방지한다.
그리고 여기서 text 변수는 xss_filter 함수의 text 매개변수로 사용될 것입니다.
[2] 공격 시도

/vuln 페이지에서
/vuln?param=<script>alert(1);<script> URL 뒤에 입력해주었더니
역시 'script'가 필터링되어서 나오는 것을 확인할 수 있었다.
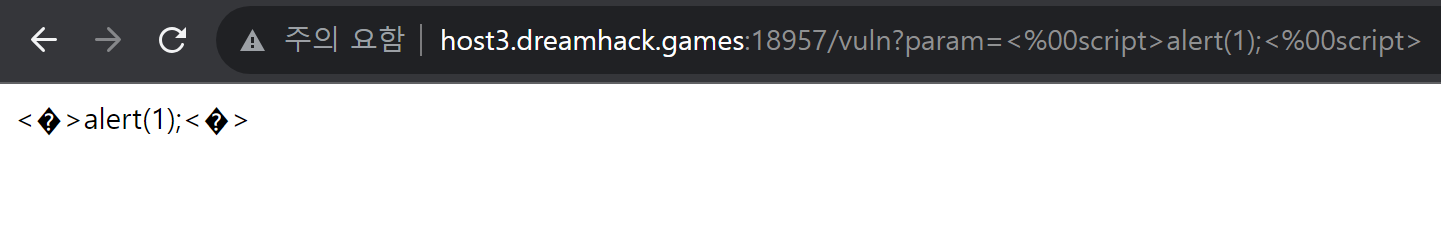
NULL(%00)을 사용했더니 깨짐 현상이 발생한다.
사용할 수 없다.
(나중에 보니까 스크립트 태그 닫는 부분에 </script>에서 '/'이 빠졌다...ㅎㅎ 그리고 %00 바로 다음에 문자 하나를 입력시켜줘야 하는 것도 까먹었다... 어찌되었든 NULL을 사용하면 깨져서 script는 인식이 안 됨!)

왕!
필터링 되는 키워드 사이에 새로운 키워드를 넣어두는 경우 우회가 가능한 문자열 치환 방법을 사용했더니 공격에 성공하였다!
그렇다면 공격은 문자열 치환 방법을 사용하면 된다.
이제 전에 풀었던 xss 문제에서 <svg onload="location.href = '/memo?memo=' + document.cookie"> 코드에 문자열 치환 방법을 적용시켜
쿠키 값에 저장된 flag값을 읽어올 것이다.
<svg oonnload="locatioonn.href = '/memo?memo=' + document.cookie"> 를 입력해주면 된다.
(처음에 location에도 'on'이 들어간 것을 놓치고 계속 "hello"가 출력되어서 당황했다.)

풀이 완료!

[3]느낀 점
오랜만에 파이썬 코드를 유심히 들여다보니 배웠던 기억이 다시 났다.
함수와 변수가 선언되고 호출되는 유기적인 과정을 따라가는 것이 나름 재미있었던 것 같다.
왜 보통 python을 사용하여 애플리케이션 파일을 만드는지가 궁금하다. (파이썬의 기능이 다양해서 그런 것일까?)
'SWLUG > 웹 해킹' 카테고리의 다른 글
| [Dreamhack/드림핵] csrf-2 (1) | 2023.11.11 |
|---|---|
| [Dreamhack/드림핵] csrf-1 (0) | 2023.11.10 |
| [webhacking.kr] Challenge old-23 (0) | 2023.11.09 |
| [Dreamhack/드림핵] xss-2 (0) | 2023.11.06 |
| [xss-game] Level 5: Breaking protocol (3) | 2023.11.06 |